“Which is it going to be, that’s all? The conspiracy or the f*ck-up?” –John LeCarré, The Honorable Schoolboy
Not that I’m jaded. Or cynical. In any case, the quotation in the headline is not from Lincoln, like so many other quotes from Lincoln that are not[1]; that was the catchphrase that came to hand with “ballot” in it. In any case, let’s hope it’s true, provenance aside.
If the legitimacy of election 2024 is to be contested, by either (any) Party, balloting issues and claims are likely to figure largely in the discourse, and in whatever measures each party takes, as they did in 2000, 2004, 2016 (in the electoral college), and 2020 [2]. In this post, I will not look in any detail at current ballot-related legal challenges; the numbers exceed my capacity, so it makes more sense to see what shakes out. In any case, many if not most of them are frivolous (and that goes twofold, threefold, tenfold for unauthenticated — “Look! A truck! By the side of the road!” — videos on the Twitter. When “citizen journalism” actually becomes journalism, that’s gonna be great, but we are so not there yet).
Instead, to aid understanding the debacle I devoutly hope will not happen on Election Day and days following, I will first look at the inordinate complexity (hence vulnerabilty) of our balloting systems; there’s rather a lot of it. I will then take a cursory, swift look at current controversies in swing states. I’ll conclude with the hope that if there is a debacle, we’ll learn from it MR SUBLIMINAL Fat chance!
Complexities and Vulnerabilities of our Balloting System
First, let’s check in with the spooks, starting with a handy Diagram from the Department of Homeland Security:
Let’s not think of this as just a diagram; let’s think of it — as the spooks probably do — as a map of attack surfaces, which I’ve helpfully highlighted. At the bottom of the diagram, highlighted in yellow, we have traditional (non-digital) methods, all of which were executed in Ohio 2004: “equipment” (which can be concentrated in favored precincts, thinned out in disfavored ones, or fail altogether, depending), “voting locations” (ditto), “opening and closing polls” (ditto), “processing votes” (slow or fast, depending), and “publishing unofficial results” (as FOX did in Florida 2000, causing Gore to concede, though he later unconceded). At the top of the diagram, in red, I have underlined modern (digital) methods: online registration, voting machines, optical scan voting ballots, DRE machines, Optical Scans, Email, Fax, “Electronically,” and audits (because IIRC some audits simply consist of running the ballots through a scanning machine as a second time.
Past use of traditional attack surfaces proves that, no matter how trustworthy the vast majority of election workers are, wrongdoing still happens (“If men were angels, no government would be necessary”).
For digital attack surfaces, suffice to day that digital = hackable, by definition (Edgers Dijkstra: “Program testing can be used to show the presence of bugs, but never to show their absence”, a bug being a potential attack surface for a bad actor. Ken Thompson: “The moral is obvious. You can’t trust code that you did not totally create yourself. (Especially code from companies that employ people like me.)”[3]
Now let’s look at the Brennan Center (more here), who assure us that everything is hunky-dory:
Since 2020, the nation’s electoral apparatus has upgraded its equipment, tightened its procedures, improved its audits, and hardened its defenses against subversion by bad actors, foreign or domestic. Ballot tabulators [but not voting machines?] are air-gapped from the Internet [how about USB sticks] and voter-verified paper records are the norm.
Let’s stop right there. By “voter-verified paper records” the Brennan Center means that the voting machine prints out a paper ballot (in essence, a receipt) so that the voter can “verify” a print-out against the choices they made on screen. There are two difficulties with this. First, many people simply trust the machine and don’t do the check at all (do you carefully verify every receipt you are given?). That opens the way for a stochastic process where some altered votes slip through due to a hacked system. There are two additional problems, depending on the architecture used. (1) If, as in the VSAP system used in Los Angeles, the voting machine transmits results digitally to the ballot counter, and then, in parallel, prints out a receipt for the voter, the real ballot is the digital transmission, not the paper receipt. The two don’t have to match, the voting machine could have been hacked, and so there is no verification at all. (2) If the voting machine prints out a receipt and then, in sequence, the receipt is scanned by a digital ballot counter, that simply moves the digital attack surface to the ballot counter.
Needless to say, I don’t find that underlined sentence from the Brennan Center a confidence builder. But let’s go on:
At the heart of that system are nonpartisan election officials at the federal, state, county, and local level who are dedicated to delivering a free and fair election. Poll workers will verify the identity and registration of every person who casts a ballot, in person or by mail. When polls close on Election Day, sooner in some states, election workers will begin tabulating early and mail-in ballots and in-person votes, usually on [hackable] scanning machines. As they proceed, officials will secure counted ballots, compile the results from the [hackable] tabulation machines, and save worksheets and (for 98% of votes cast[4]) paper records for official and public review. The entire procedure is overseen by poll watchers from both parties.
I yield to nobody in my admiration for the church ladies who carefully cross my name off the registration list, hand me my paper ballot, and then give me my “I voted” sticker (and I think hassling them is really vile, and should stop). That said, the key issue is not how the system operates on the whole and on the average. In an election that (almost) universally expected to be close, only a few insiders in a few precincts in some of the seven swing states are required to hack the outcome (and you can bet that there are “black hats” whose very expensive business it is to know those insiders, those precincts, those states, and, of course, the hack. And very few of them go up in small planes). And finally:
No human enterprise that spans tens of thousands of polling places, hundreds of thousands of election officials, and more than 150 million projected voters can aspire to be flawless, says Jen Easterly, a former Army intelligence officer who directs the Cybersecurity and Infrastructure Security Agency (CISA). “There could be a ransomware attack on an election office,” Easterly says. “There could be a distributed denial of service attack on a website, so you can’t see election-night reporting. Somebody will forget their key to a polling place, so they could open late. A storm may bring down a power line, so a polling place needs to be moved.”
(We will see in a moment how disingenuous the Brennan Center is, describing CISA’s Easterly as “former Army intelligence officer.” The New Yorker played the same trick with FMIC’s Jessica Brandt). I also yield to nobody in my admiration for election workers generally, and in my frustration at the enormous number of human errors that get blown up into malfeasance on social media, generally without attestation. More:
What matters, she says, is that election officials have trained for all those contingencies. “They are prepared to meet the moment and to deal with any disruption,” she says. Easterly and her state counterparts play this message of reassurance on repeat, interview after interview and speech after speech. It has the virtue of being true. There really are playbooks and backup procedures and well-designed mitigation plans for every bad thing they have ever seen happen to an election, and none of those bad things pose a genuine threat to the integrity of the vote.
“Every bad thing”? No. Except for one. Can you guess? Take a moment:
Quis custodiet ipsos custodes ? (“Who watches the watchers“, Juvenal, c. 100 AD).
100AD, what would be… 2024 – 100 = 1924 years ago. That’s a lot! And Jen Easterly “was deployed to Baghdad as chief of the cryptologic services group for the National Security Agency. She also worked for NSA’s elite Tailored Access Operations,” the “hacking unit” exposed by Edward Snowden, that infiltrated computers around the world. Clearly, if there’s a “watcher” who, wearing a White Hat, is equipped to protect all those digital attack surfaces, it’s Jen Easterly. Equally clearly, if there’s a watcher who, wearing a Black Hat, is equipped to hack them, it is also Jen Easterly[5]. That would be a Bad Thing. And yet hacking, in general, goes unmentioned both by the Brennan Center and Easterly. Odd!
Now, I would never attribute means (***cough*** Tailored Access ***cough***), opportunity (***cough*** CISA directorship ***cough***), or motive (***cough*** Orange Hitler ***cough***) to Easterly without any evidence. But I don’t have to. We’re talking systems, not persons. The principle to keep in mind here is Akerlof and Shiller’s “Phishing Equilibrium” (see NC here, here, and here), which I summarize as: “If fraud can happen, it will already have happened.” The same principle applies in the famous joke about the two economists walking down the street. One spots a twenty dollar bill lying in the street, and bends to pick it up. The other stops him, saying “If that twenty were real, somebody would already have picked it up.” Every digital attack surface could be that real twenty dollar bill. The goal of election security, therefore, should not be to create a three-ring binder with a page for every contingency — except, naturally, for Black Hat insider attacks, because who knows, we might need them some day — but to simplify the system so the number of attack surfaces is as minimal as possible. Why leave twenty dollar bills on the street?
And speaking of twenty bucks lying in the street, here’s a tweet from Marc Elias, Democrat election lawyer extraordinaire and the cut-out through whom the Clinton campaign laundered its payments to spook Christopher Steele, of dossier fame. Democracy Docket is Elias’s website:
NEW: A record setting 200 voting and election cases have been filed in 2024. The states with the most:
Pennsylvania 27
Georgia 24
Nevada 15
Wisconsin 14
Arizona 13For a limited time, Democracy Docket is offering $20 off premium membership. https://t.co/2Scval9aLm
— Marc E. Elias (@marceelias) November 2, 2024
The Harris campaign has a billion dollars and counting, unless they’re lying. Are they paying Elias in such meagre coin that he’s got to hit up the rubes? With that, let’s turn to the Swing States.
Recent Balloting Issues in Swing States
Let me caveat once more that I make no attempt to be exhaustive; the tweets that follow are simply the latest Swing State-related froth from my Twitter timeline. However, readers, if you live in any of these seven states and have anecdotes or links you wish to share in comments, please do so!
Arizona
Curing ballots:
Swell, if it’s non-partisan, which this clearly is not.
Georgia
“Georgia judge says voters can hand in mail ballots in rejection of GOP lawsuit” [FOX]. “A judge in Georgia on Saturday dismissed a Republican lawsuit that sought to block voters from hand-returning mail-in ballots in the state over the weekend…. A Fulton County spokesperson said on Saturday afternoon that only a couple dozen ballots had been returned to the four open county offices.” • To me, the same as above. Commentary:
Georgia judge says voters can hand in mail ballots in rejection of GOP lawsuit
Here we come go again!
Last minute changes in voting rules by Democrat
supportive Judges.
It also happened in 2016 and 2020 Presidential elections.https://t.co/iF8gogd43U
— Thomas G (@Thomasguam) November 3, 2024
I understand the point about last-minute rule changes, but I see this as a problem of not being able to determine all the edge cases in an absurdly complex system, rather than as malfeasance.
“Republicans score victory in Georgia fight over election observers, RNC chairman says” [FOX]. “Georgia Secretary of State Brad Raffensperger said on X, ‘We’re pleased that Fulton County has implemented our requirement allowing monitors in the spirit of Georgia law. But we are concerned that this was ever a question in the first place.’ The alleged exclusion of poll watchers from the weekend absentee ballot submission hours was not limited to just the GOP. It included all observers, Republicans said. An RNC spokesperson told Fox News Digital having public poll observers through the weekend benefited both Republicans and Democrats but argued their absence would hurt the GOP more in left-leaning areas. The spokesperson said the RNC worked with Georgia election officials to secure access for poll observers.” • Poll watchers are good, unless and until they morph into a “bourgeois riot,” as in Miami 2000, or similar levels of officiousness.
Michigan
“Spreadsheet showing Michigan voter data isn’t proof of election fraud” [WTSP]. “Recent social media posts alleging election fraud in Michigan have gone viral as millions of Americans cast their ballots. The posts show a spreadsheet with Wayne County, Michigan, addresses and voter ID numbers. In the image, a highlighted voter ID column appears to show the same ID assigned to multiple addressees, suggesting one person has cast multiple votes…. The image is not proof that any individual in Wayne County, Michigan, cast multiple votes. A formatting error in the state’s voter registration database mistakenly made it look like people voted multiple times, Michigan election officials and Republican National Committee Co-Chair Lara Trump confirmed. The error has since been corrected and each voter listed in the report only voted once in the election, officials said.” • Commentary:
Our election integrity team received reports of thousands of duplicate ballots in Michigan.
We immediately investigated and have CONFIRMED that it was a glitch in the system – these duplicates were not and WILL NOT BE COUNTED.
We are on it and protecting the vote! https://t.co/F73rzmsBRL
— Lara Trump (@LaraLeaTrump) October 30, 2024
Nevada
“Nevada’s high court allows counting of mail-in ballots without postmarks” [Politico]. “The Nevada Supreme Court has turned down a bid by Donald Trump’s campaign to block state officials from counting mail-in ballots that lack postmarks but arrive within three days after Election Day… The court’s majority said adopting the GOP position could disenfranchise some voters through no fault of their own. The ruling affects only a small number of ballots that arrive by mail but lack postmarks due to what the majority called ‘random postal service omissions.’” • The decision looks fine to me — readers? — if you accept the proposition that mail-in ballots shold be normalized, and if indeed the omissions are random (“small” is not relevant. The margins are small!)
North Carolina
Ballot selfies:
AGAIN, PLEASE.. CHECK TO SEE IF RECORDING, TAKING A PICTURE WITH YOUR BALLOT IS LEGAL IN YOUR STATE! It is illegal IN NORTH CAROLINA to do a “ballot selfie” or recording and can be cause for invalidation..
I DON’T WANT ANY JUSTIFICATION FOR INVALIDATION, PLEASE CHECK YOUR STATE.
— Olli at the Clock Shop (@llhall2) October 21, 2024
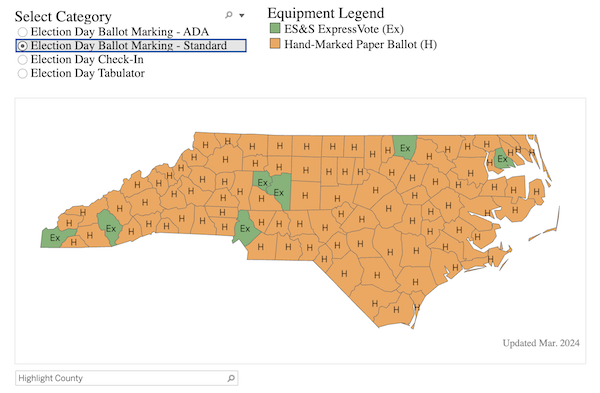
“Election Day Voting Equipment by County” [North Carolina State Board of Elections]. This is an impressive piece of work:
Note, however, that the ADA ballot marking is done digital, and I cannot find what the standard is for voting on paper vs. voting on machine.
Pennsylvania
“Supreme Court rules Pennsylvania may count back-up votes when mail ballots are rejected” [CNN]. “The US Supreme Court on Friday left in place a Pennsylvania court ruling that is expected to expand options for voters whose mail-in ballots are rejected for technical reasons to have their votes counted, in a defeat for Republicans in a critical battleground state. There were no noted dissents. For Pennsylvania voters who made a mistake in how they prepared their mail-in ballots, it could ensure they have a backup option to have a provisional ballot counted…. It’s unclear how many Pennsylvania voters will benefit because not every county notifies voters of defective mail ballots. But both sides in the appeal before the Supreme Court characterized the dispute as affecting potentially “thousands” of votes at a minimum…. Different counties in Pennsylvania have different procedures for dealing with defective mail ballots, some more forgiving than others. That patchwork of rules makes it difficult to say with certainty how many ballots were at stake in the case.” • Looks like a mess.
Wisconsin
“Pro-Trump poll watchers primed for Election Day action in key state” [Reuters]. “Many local officials fear the activist action at election sites, while limited, was merely a rehearsal for a much larger-scale event on Nov. 5, when Republican Trump goes up against Democrat Kamala Harris in the fight for the White House. ‘It was absolutely a dry run for the general election,’ Glendale’s Democratic Mayor Bryan Kennedy told Reuters, adding that police were called to two polling stations by election workers and ordered two observers to leave, when it was decided the ballot challenges were without basis. ‘They were challenging every absentee ballot with whatever reason they could pull out of thin air,’ Kennedy said. With days to go until the presidential vote, opinion polling shows the election is on a knife-edge, with few places as pivotal as Wisconsin.” • Thousands of Marc Elias mini-mes? What a prospect. And then there’s this:
MAGA Wisconsin Election Commission director Kimberly Zapata found guilty on all felony counts for falsifying military ballots. She could face 5 years in prison pic.twitter.com/p1nwgR52Yj
— KamallaDreams (@KamalaDreams) October 31, 2024
Life’s rich pageant!
Conclusion
Of course, as I urged here (“The Organs of State Security Involved in Authenticating Election 2024 (or Not)“, and back in 2016, here (“Federalist 68, the Electoral College, and Faithless Electors“) the over-riding issue, the change in our Constitutional order, comes from putting the spooks in charge of authenticating our elections. What happens, to invent a not-entirely-implausible scenario, if Trump wins because of a 10,000-vote margin in Pennsylvania, but an anonymous leak to the New York Times on “The Day After” claims those 10,000 votes were the result of a hack? And then, after a week or so of hysteria, it turns out that the source of the leak is Jen Easterly, late of NSA’s Tailored Access Operations, who assures us it’s all true, really, but can’t reveal intelligence sources and methods? Granted, this is rank speculation. But do we want a system where such speculation is even possible? Because that’s the balloting system we have.
The obvious solution is to have elections that are validated by citizens, not spooks (as I wrote in “What “Our Democracy” Should Look Like When Voting: A Simple Plan). In essence: Ballots should be hand-marked on paper and counted in public. All voting should take place on the same day. Election Day should be a national holiday (with much more detail in the post). Keep it simple, stupid!
Take digital out of the equation, you take the spooks out of the equation, and you save the Constitutional order. What’s not to like?
NOTES
[1] Quote.org shows that Lincoln used this “bullet”/”ballot” antithesis numerous times — and no wonder — but “The ballot is stronger than the bullet” has no cite. Hilariously, Google’s alternative, “To give victory to the right, not bloody bullets, but peaceful ballots only, are necessary,” has no cite either. “Ballots are the rightful and peaceful successors to bullets,” implying the civilization advances, comes from Lincoln’s Message to Congress, July 7, 1861.
[2] It seems to me likely that Democrats, in the event of a Trump victory, would not make the main thrust of their assault within the judicial branch, given the composition of the Supreme Court; see here. Republicans might well do so, given the same givens.
[3] One of the most offensive butcheries of Trump’s farcical butchery of the 2020 election challenges — which may have turned paper ballots into a partisan issue, setting it back by a generation, good job Don — was his failure to demand voting machine source code. How on earth can we even begin to know it’s secure without examining it?
[4] With election margins as thin as they are, that 98% figure seems a little sus.
[5] Are we really to believe that the NSA’s Tailored Access Operations unit has not hacked voting machines in Color Revolutions abroad? Heck, what good are they if they haven’t? But who watches the watchers to make sure those hacks don’t go domestic? Especially when “President Hitler” could undoubtedly be framed as a national security issue, say by a “thirty-five year national security expert“?